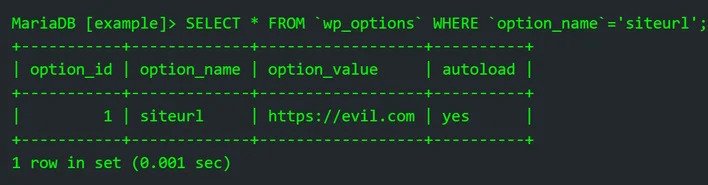
Unknown hackers are taking advantage of a security vulnerability in the Elementor Pro website builder plugin for WordPress, which could impact millions of sites worldwide. The flaw, which affects versions 3.11.6 and earlier, allows an authenticated attacker to take over a WordPress site that has WooCommerce enabled.
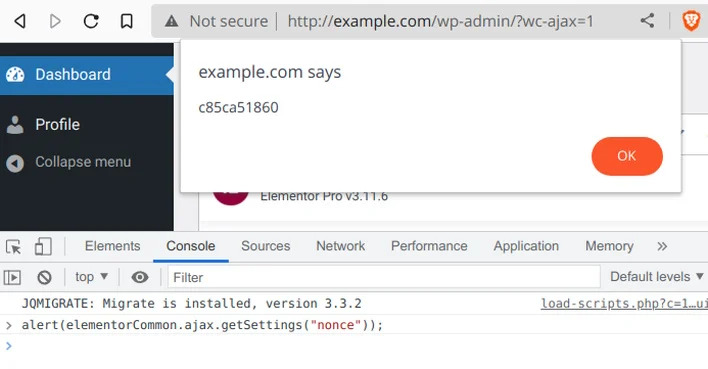
According to reports, the vulnerability was discovered and reported by security researcher Jerome Bruandet, and was patched in version 3.11.7 released on March 22. However, Patchstack has warned that the flaw is still being actively exploited by several IP addresses, with hackers attempting to upload arbitrary PHP and ZIP archive files.
As a result, users of the Elementor Pro plugin are strongly advised to update to the latest version, 3.12.0, or at least version 3.11.7, as soon as possible to mitigate the risk of potential attacks. Failure to do so could result in malicious users creating an account with administrator privileges, turning on the registration page (if disabled), and uploading malicious plugins or backdoors to further exploit the site.
The advisory comes just over a year after a critical vulnerability was found in the Essential Addons for Elementor plugin, which could result in the execution of arbitrary code on compromised websites. WordPress has also recently issued auto-updates to remediate another critical bug in the WooCommerce Payments plugin, highlighting the importance of keeping all plugins and software up to date to avoid falling victim to cyber-attacks.




